Task 05 - Deploy and configure Azure Firewall
Introduction
Tailspin Toys is migrating their on-premises SQL Server database to Azure SQL Managed Instance. In this task, you will implement an Azure Firewall to protect network traffic.
Description
In this task, you will implement an Azure Firewall to protect network traffic.
The key tasks are as follows:
- Test network traffic from the Virtual Machine to the Internet. You should have access to bing.com.
- Deploy Azure Firewall.
- Configure rules to block access to bing.com.
- Test network traffic from the Virtual Machine to the Internet. Access to bing.com is now blocked.
Success Criteria
- Azure Firewall is deployed and fully worked as expected.
Solution
Expand this section to view the solution
-
Sign in to the Azure Portal.
If you’re using Azure Gov, sign in to the Azure Gov Portal.
-
Connect to the tailspin-webapp-vm and using Microsoft Edge navigate to https://www.bing.com. You should be able to access Microsoft Bing.
-
In the Azure portal, in the Search resources, services, and docs text box at the top of the portal, search for tailspin-hub-vnet, then select the found Virtual Network.
-
Under Settings, select Subnets and then the + Subnet option.
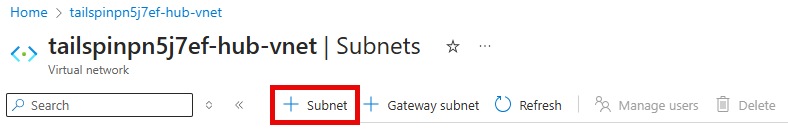
-
On the Add a subnet pane, enter the following values, then select Add.
- Subnet purpose: Select Azure Firewall.
- IPv4 Starting address:
10.1.100.0/24
-
In the Azure portal, in the Search resources, services, and docs text box at the top of the portal, search for Firewalls, then select the Firewalls service.
-
On the Firewalls page, select + Create.
-
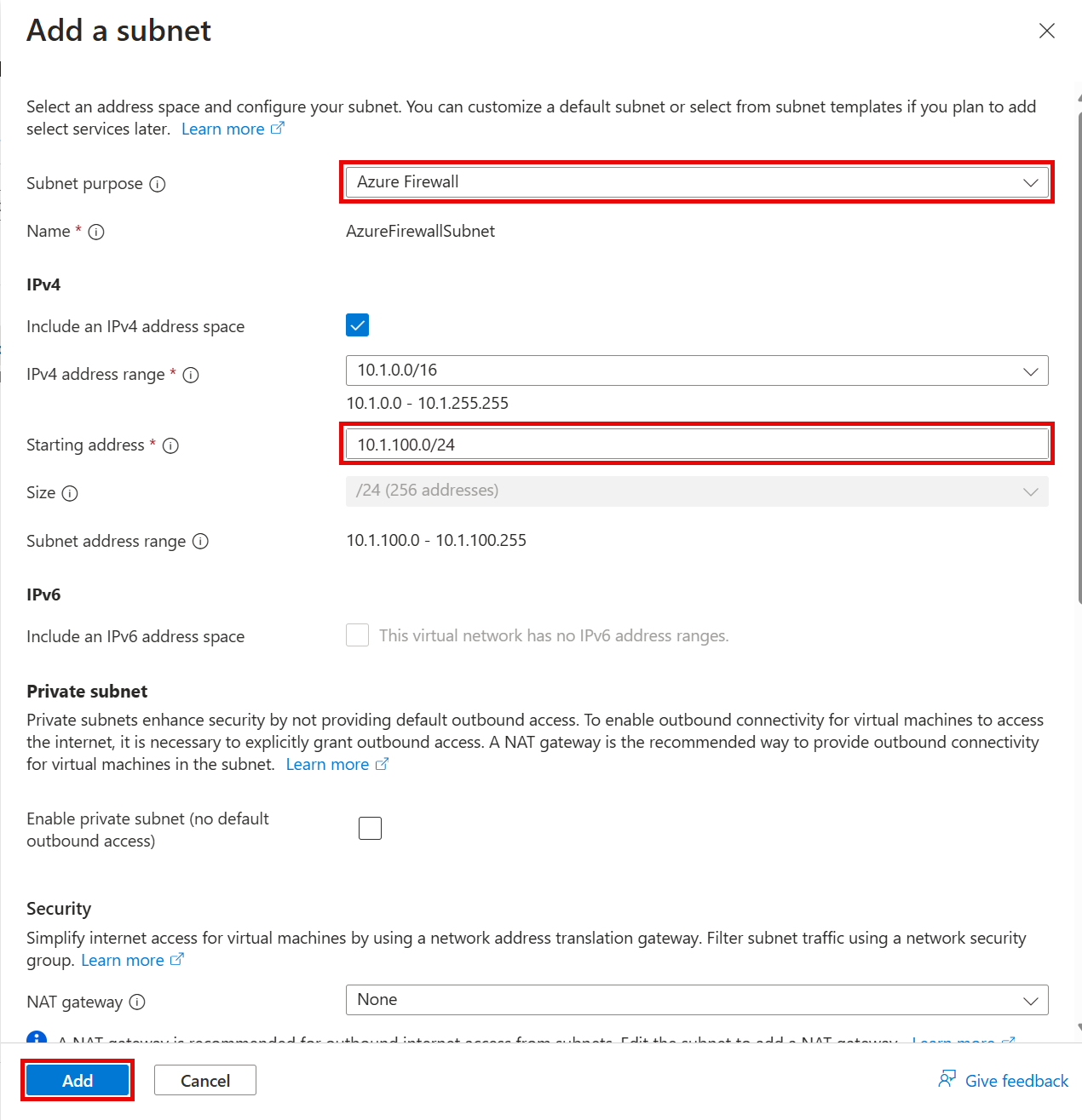
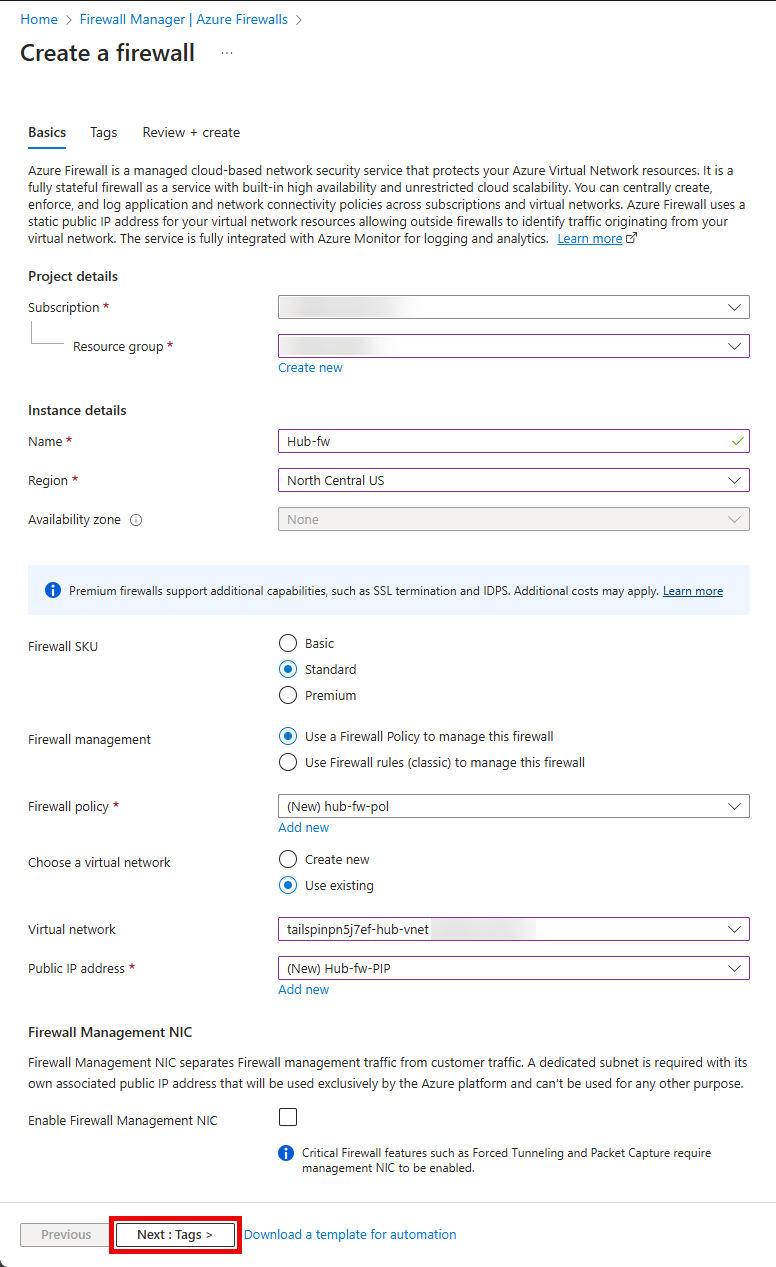
On the Basics tab, enter the following values, then select Add new on the Firewall policy section.
- Resource group: Select the Resource Group created for this lab. For example:
tailspin-rg. - Name:
Hub-fw - Region: Select Sweden Central.
- Firewall SKU:
Standard - Firewall management:
Use a Firewall Policy to manage this firewall
- Resource group: Select the Resource Group created for this lab. For example:
-
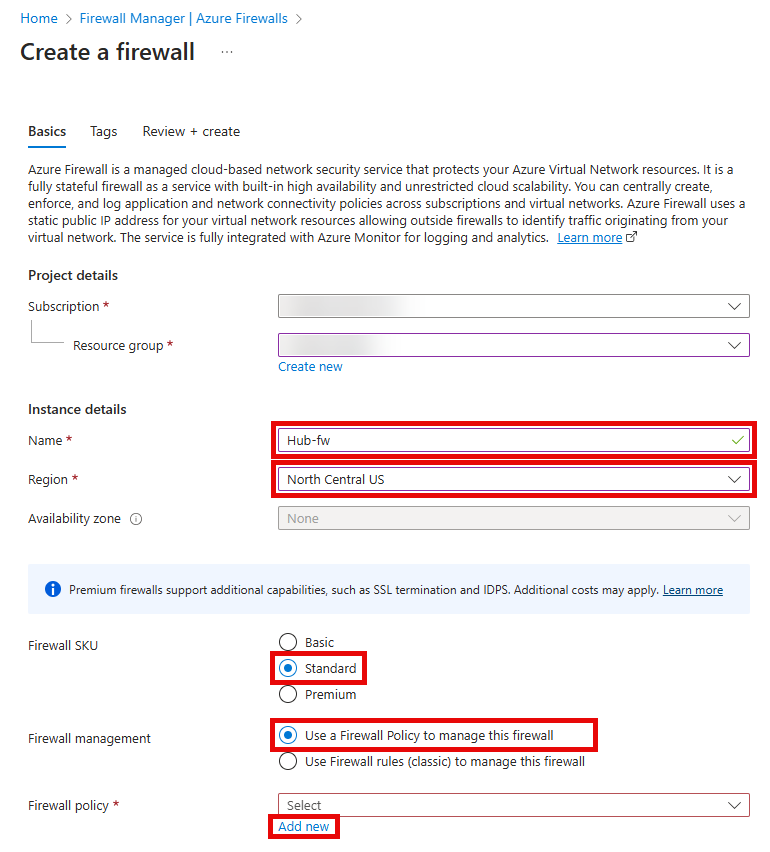
On the Create a new Firewall Policy popup, enter the following values, then select OK.
- Name:
hub-fw-pol - Region: Select Sweden Central.
- Name:
-
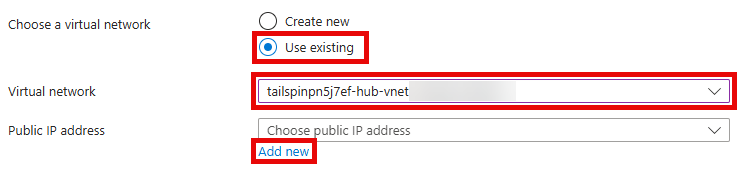
On the Basics tab, enter the following values, then select Add new on the Public IP address section.
- Choose a virtual network:
Use existing - Virtual network:
tailspin-hub-vnet
- Choose a virtual network:
-
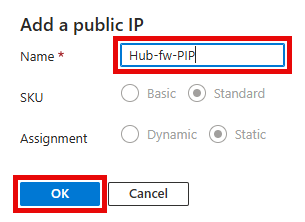
On the Add a public IP popup, enter the following values, then select OK.
- Name:
Hub-fw-PIP
- Name:
-
On the Basics tab, ensure that the Enable Firewall Management NIC option in
Not Checked.
-
Review the values entered, then select Next : Tags >.
-
On the Tags tab, select Next : Review + create >.
-
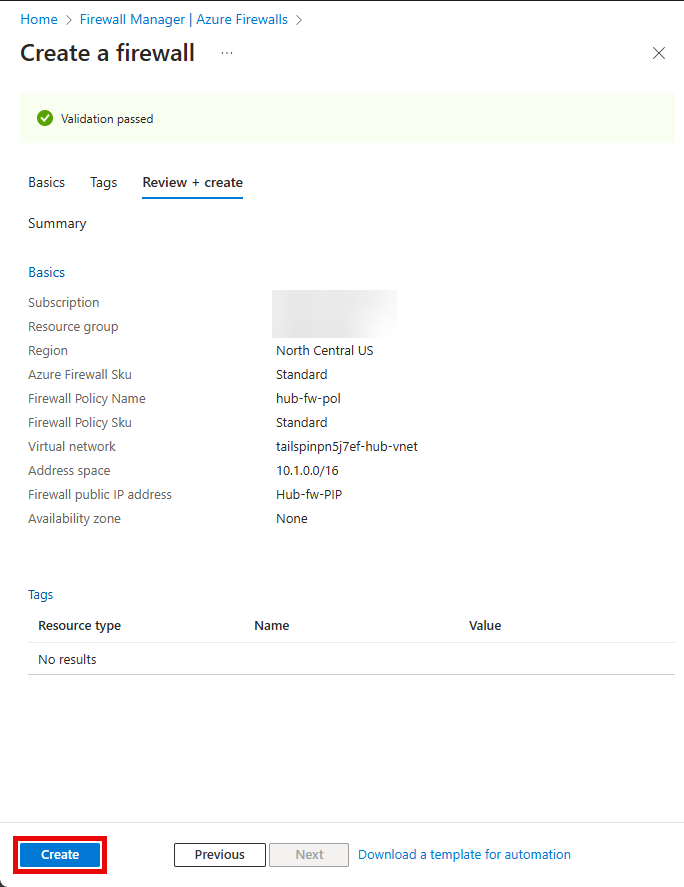
Once the validation passes, select Create.
Wait for the deployment to complete. This should take about 5 minutes.
-
In the Azure portal, in the Search resources, services, and docs text box at the top of the portal, search for Resource groups and press the Enter key.
-
On the Resource groups blade, in the list of resource group, select tailspin-rg entry.
-
In the list of resources, select the entry representing the Hub-fw firewall.
-
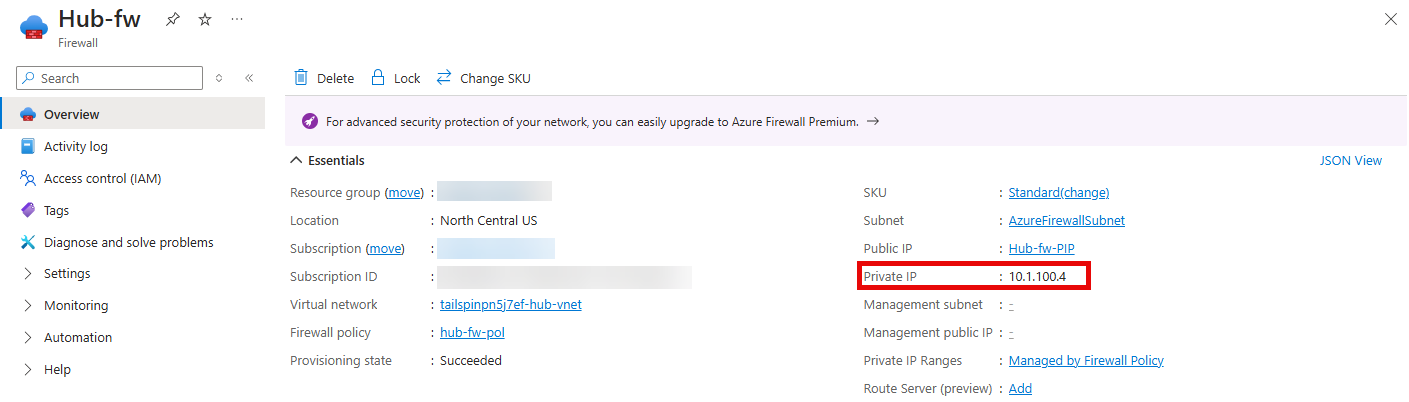
On the Hub-fw blade, take note of the Private IP address that was assigned to the firewall.
-
In the Azure portal, in the Search resources, services, and docs text box at the top of the portal, search for Route tables, then select the Route tables service.
-
On the Route tables blade, select + Create.
-
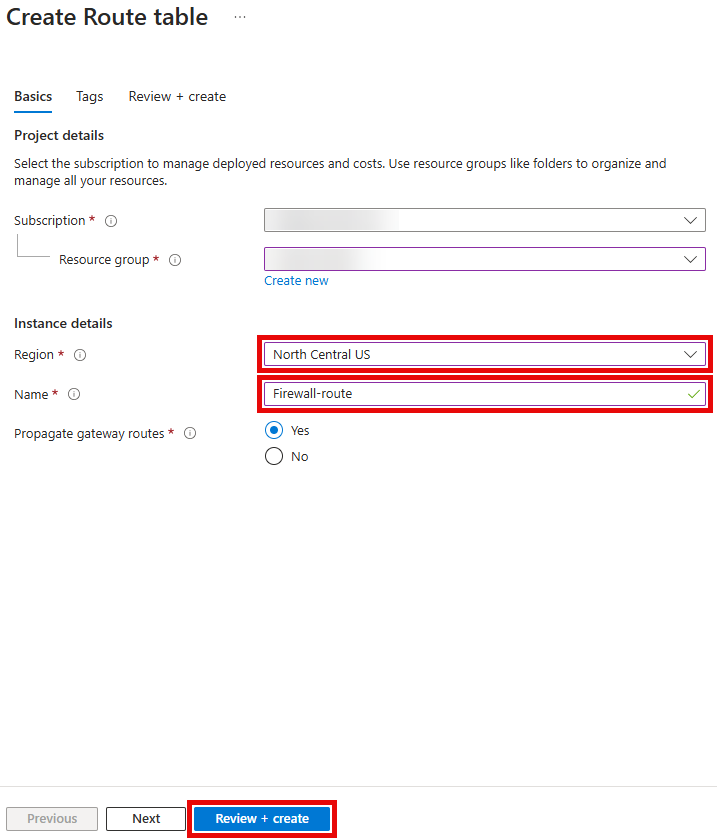
On the Create Route table pane, enter the following values, then select Review + create, then select Create.
- Resource group: Select the Resource Group created for this lab. For example:
tailspin-rg. - Region: Select Sweden Central.
- Name:
Firewall-route
- Resource group: Select the Resource Group created for this lab. For example:
-
On the Route tables blade, click Refresh and, in the list of route tables, select Firewall-route.
-
On the Firewall-route blade, in the Settings section, select Subnets.
-
On the Firewall-route | Subnets blade, select + Associate.
-
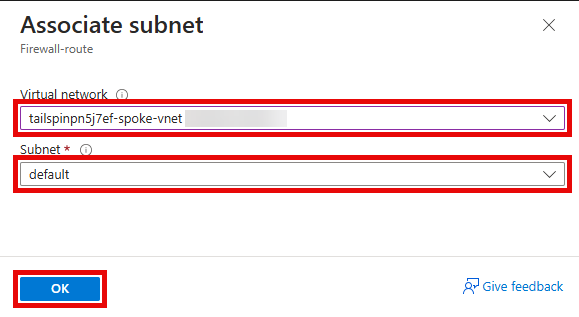
On the Associate subnet pane, enter the following values, then select OK.
- Virtual network:
tailspin-spoke-vnet - Subnet:
default
- Virtual network:
-
On the Firewall-route blade, in the Settings section, select Routes.
-
On the Firewall-route | Routes blade, select + Add.
-
On the Add route pane, enter the following values, then select Add.
- Route name:
FW-DG - Destination type:
IP Addresses - Destination IP addresses/CIDR ranges:
0.0.0.0/0 - Next hop type:
Virtual appliance - Next hop address: The private IP address of the firewall that you identified in the previous when creating the Azure Firewall. For example:
10.1.100.4
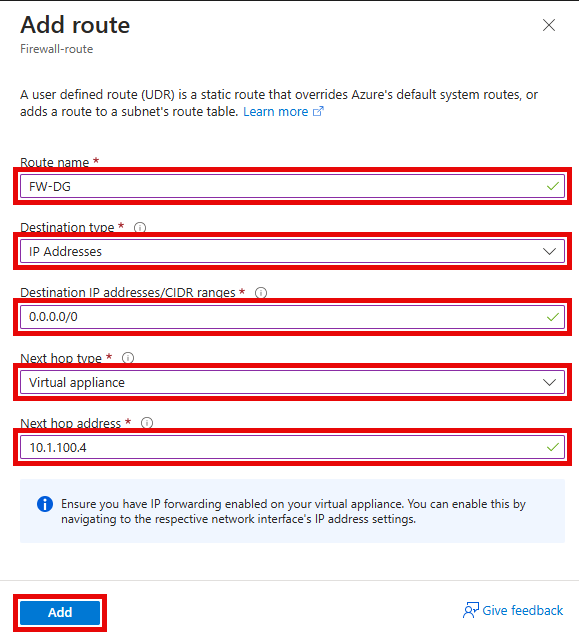
Azure Firewall is actually a managed service, but virtual appliance works in this situation.
- Route name:
-
Connect to the tailspin-webapp-vm and using Microsoft Edge navigate to https://www.bing.com. You should NOT be able to access Microsoft Bing.
-
In the Azure portal, navigate back to the Hub-fw firewall.
-
On the Hub-fw blade, in the Firewall policy section, select hub-fw-pol.
-
On the hub-fw-pol Firewall Policy blade, in the Settings section, select Application rules.
-
On the hub-fw-pol | Application rules blade, select + Add a rule collection.
-
On the Add a rule collection pane, enter the following values.
- Name:
App-Coll01 - Priority:
200 - Action:
Allow

- Name:
-
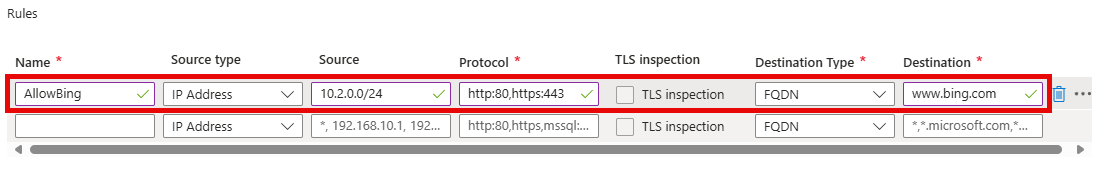
On the Rules section, create a new entry with the following values, then select Add.
- Name:
AllowBing - Source type:
IP Address - Source:
10.2.0.0/24 - Protocol:
http:80,https:443 - Destination Type:
FQDN - Destination:
www.bing.com
- Name:
-
Connect to the tailspin-webapp-vm and using Microsoft Edge navigate to https://www.bing.com. You should be able to access Microsoft Bing.